Internet
Digital Signature as a Form of Authentication

Sometimes some old-fashioned techniques do not work in this modern world like making collaborations through traditional means using pen and paper. The era in which we are living demands more responsive and flexible solutions like digital signatures. Let’s take the example of a businessperson, with the business partners that are based abroad.
Whenever they need to make a deal, it can take them weeks to travel back and forth to countersign the documents. Now if these two parties use digital signatures, they could close their deals in a matter of minutes not weeks. Studies have shown that digital signatures help to save an equivalent of one whole working week per year for every working-age adult. That is what makes digital signatures so important!
Let’s discuss in detail what is digital signature and collaboration in detail, and how it works?
What is Digital Signature?
Digital signatures are one of the main aspects of ensuring the security and integrity of documents that are used in an online world. Similar to the handwritten signatures of the physical world, digital signatures are used to bind a person or entity to digital documents.
Three Main Purposes
Digital signatures and certificates are used for the following three main purposes.
1. Authentication
A digital signature helps in verifying the receiver that the claimed sender has created and sent the message.
2. Non-Repudiation
With a certified contract between the two parties, no party can disown it later on.
3. Integrity
With asymmetric key encryption, digital signatures ensure that the messages are kept safe and as it is during the transit.
Practical Demonstration with the Help of a Use Case
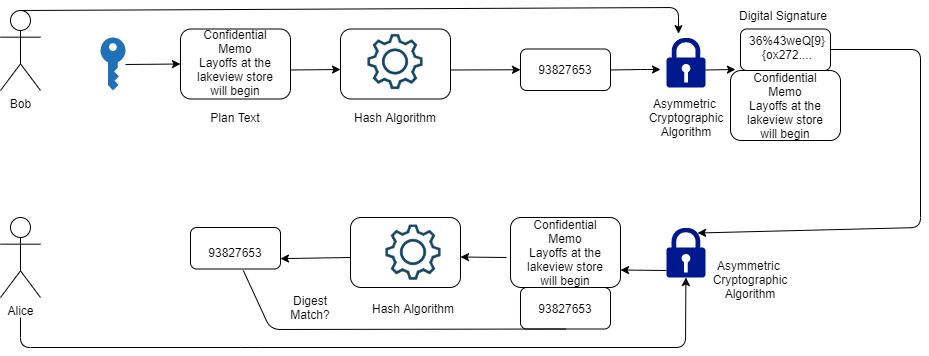
Now let’s demonstrate how digital signature works? Consider the scenario described above. Bob tends to send a memo to Alice with his digital signature on it. The digital signature used here uses asymmetric cryptography, based on the public-key algorithm. Two keys are generated by Bob, the public key, and a private key. The private key is kept with Bob and public key is sent to Alice, the receiver. After memo completion, a digest is generated at Bob’s end by hashing the memo using techniques of hashing algorithms. Finally, the digest is encrypted with Bob’s primary key.
The digest encrypted above is the digital signature of the memo. After securing the memo with the digital signature, Bob sends it over to Alice. It is to be noted here that the memo itself is not encrypted, we are only focusing on creating a digital signature.
When Alice receives the memo and digital signature, the following job is done at her end:
- Alice has Bob’s public key, which she will use to decrypt the digital signature, she will be able to access the digest. However, if Alice is not successful in decrypting the digital signature, then it means that this digital signature was not sent by Bob because there is only one public that can decrypt the digest generated by Bob’s public key.
- Since the digest was in transit from one place to another, it is important to verify its integrity. To do this, Alice applies the same hashing algorithm on the memo as Bob did and compares the results with the received digest.If the generated results are equal, it will confirm Alice that the memo has been sent by Bob, and if they are not Alice will get to know that during the transit the memo has been changed.
Improving the Collaborations Among Teams for the Future of Work
In the past year, we have seen a huge paradigm shift from physical work to remote work. There is an immense need for running some of the very important operations to run very smoothly such as contract management, signing e-documents, and sourcing operations, etc. The company plumedot provides users with a streamlined, secured, AI platform for digital signing and collaboration.
Here are some of the potential benefits of digital signatures along with their elaboration on how they can be used to ease the collaborations among different parties and teams.
- Digital ID is trusted because you can only get digital signatures only from a certified company. So involving the third party helps different teams to maintain the check and balance of the terms made between them.
- Your document and signature get encrypted, so there is a very minimum chance of information leakage.
- A new pin is generated whenever you sign the document so that your document becomes certified and unique to you.
Let’s explore some of the amazing services offered by plumedot for the digital acceleration of remote work, and collaboration among the teams.
Digital Signing: The service is readily available, and can be used anywhere, anytime.
Immutable Records: Through the advanced technology with video conferencing, your video recording of the signing ceremony is stored in one record with your signed document.
AI-Powered Platform: Your document gets certified with AI power-based solution making them more secure and reliable.
Some of the features that make plumedot unique are,
- Legally binding eSignatures
- Bank-grade security
- Robust API engines
- Simplified complex workflows
Uses of Digital Signatures
plumedot’s amazing services can be very helpful for the following major industry sectors,
- Signing documents for different eCommerce and drop-shipping stores.
- Different software distributions.
- Various types of legalities, for example, patents, copyrights, and trademarks, etc.
Conclusion
It’s a paperless world and digital transactions and document sharing are the norms. But there is a problem, digital documents are more prone to security risks than a physical paper copy delivered from place to place. That’s why digital signatures are very important. They help to prevent tempering and forgery while sending the documents from one place to another over the internet using mathematical techniques for verification and authentication. The company plumedot can be utilized for better team collaborations and agreements with more enhanced authentication and immutability.






